How to host critical applications?
Critical applications must be running at all times and can never be offline. This is the case, for example, with e-commerce, banking or emergency services. Managers of critical applications therefore have every interest in setting up this type of security system, which is much less expensive than a loss of money generated by an offline site.
What are the benefits of EXCLUSIVE SECURITY solutions for mission critical applications?
French accommodation
By hosting your files with EXCLUSIVE SECURITY, you keep your data close to you. The EXCLUSIVE SECURITY Data Centers are located in France and are governed by European laws for the protection of personal data.
Support
EXCLUSIVE SECURITY does everything in its power to provide the best possible support to its customers and ensure them the best possible experience. Technical support is available 24 hours a day, 7 days a week. In addition, thanks to various monitoring solutions for our network, the EXCLUSIVE SECURITY teams act in proactive mode as soon as a problem has been identified.
Network security
By leaving your server in a Data Center, you also take full advantage of all the security that the latter provides. The EXCLUSIVE SECURITY network is protected against DDOS attacks thanks to anti-DDOS level 3 solutions. In addition, this network is constantly tested and the multiple agreements of EXCLUSIVE SECURITY with the various operators make it possible to guarantee continuous service and quality.
Examples of infrastructureHosting critical and mission-critical applications
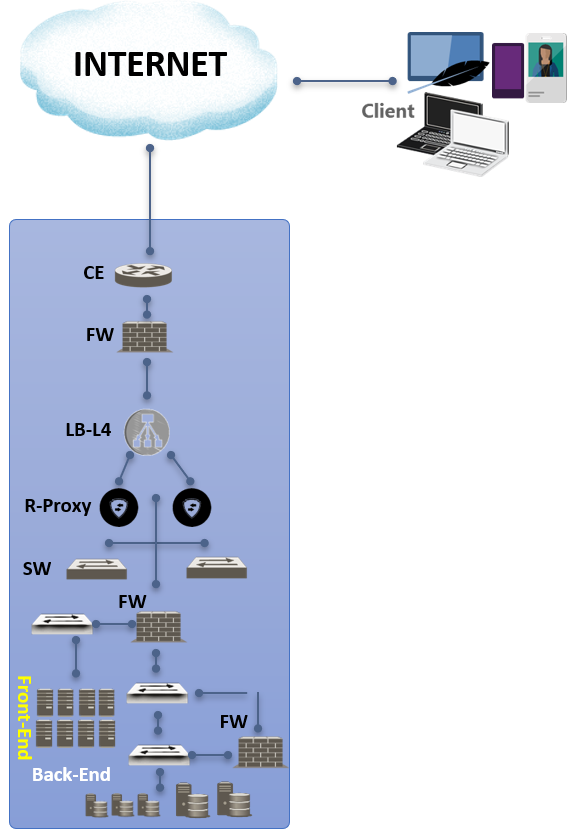
Hosting area Level 1
Ideal for sites that are not critical, but still need some security.
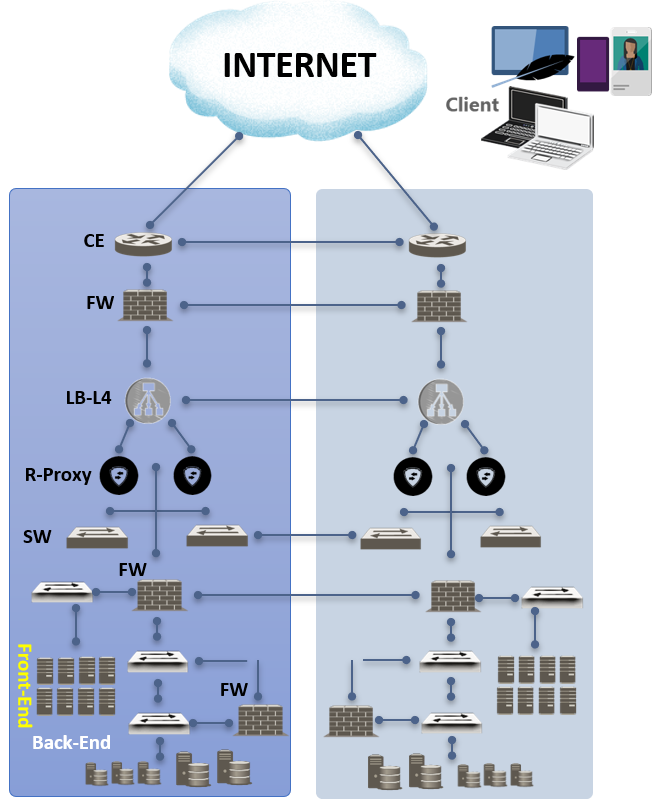
Hosting area Level 2
Suitable for high-stakes and / or critical applications, requiring high availability/redundancy
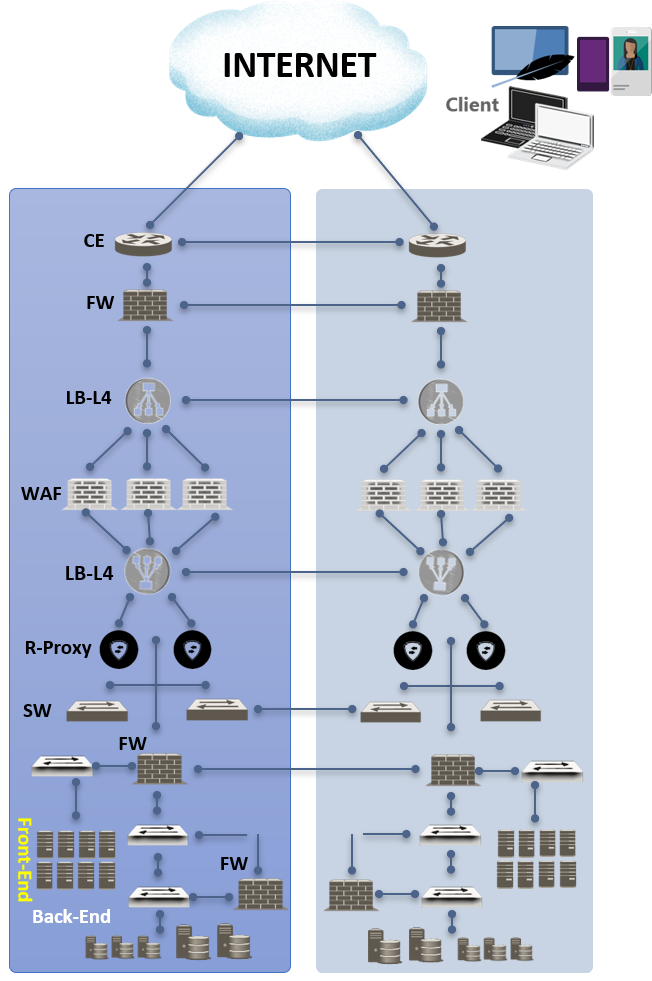
Hosting area Level 3
Corresponds to high-stakes data hosting, requiring high availability / end-to-end redundancy meeting the Security Assurance Plan (PAS) of large organizations.
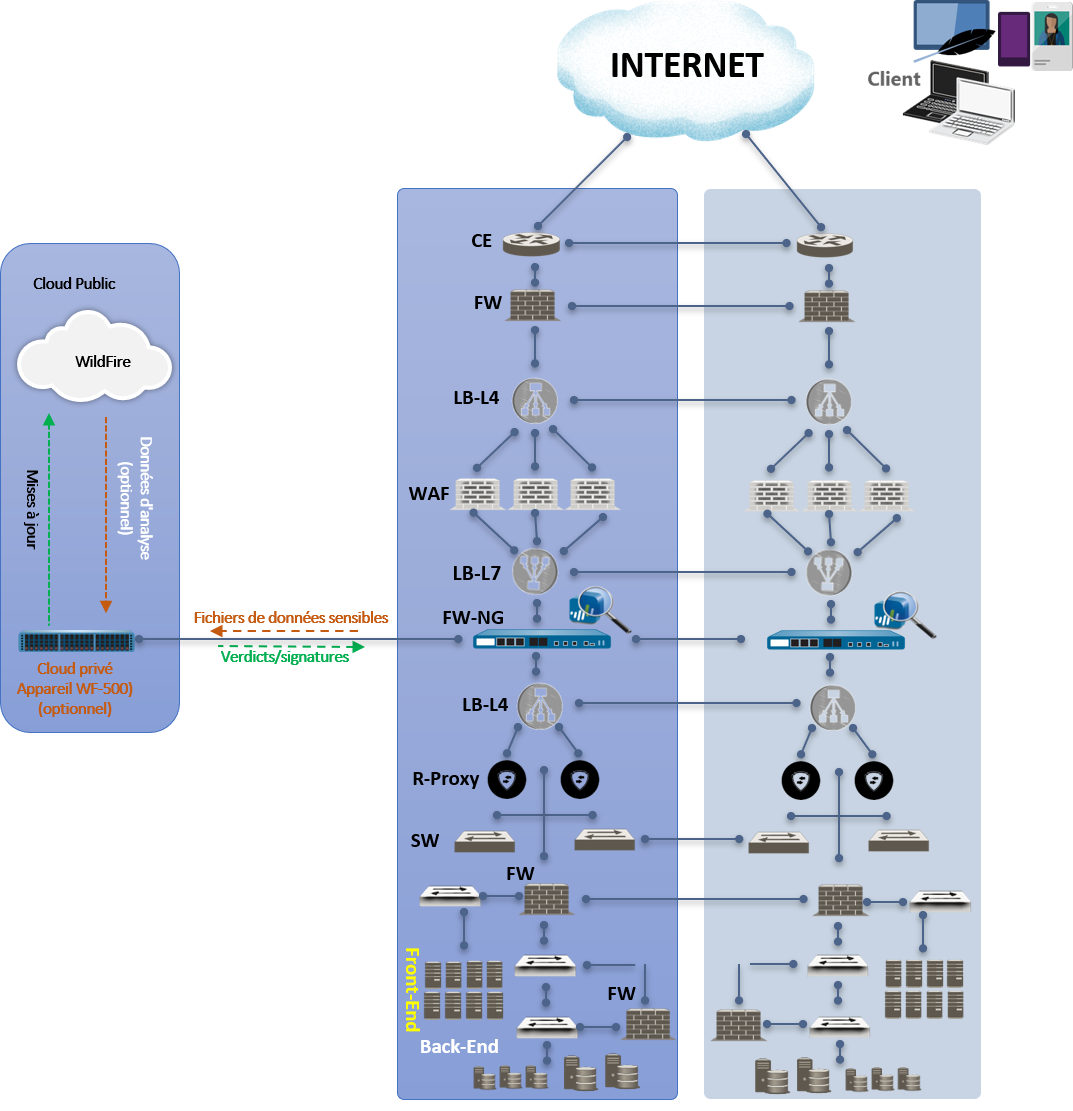
Hosting area Level 4
Addressed to critical applications with very high stakes, requiring high availability / end-to-end redundancy, and supporting high and occasional increases in load.